Security Risk and Compliance Overview
Symbl.ai conversational intelligence platform enables businesses to contextually understand natural human interactions at scale to general key insights, actions and knowledge from conversations. The platform empowers developers with a comprehensive suite of APIs and SDK that unlocks proprietary machine learning algorithms to understand, analyze and identify actionable insights from voice, text and video conversations without building ML models.
Information Security
Symb.ai encrypts and protects sensitive information across the transformation and analysis process.
- Data in Transit – TLS encryption for all data exchanged. Additional security is available for dedicated VPN connections between the customer and Symbl.ai.
- Data at Rest – AES 256 bit encryption
- Network Security – Intrusion detection systems and alerts to monitor for real-time threats, including the use of a web application firewall (WAF) and Google Cloud Armor Network Security
Access Management & Authentication
Symbl.ai’s platform provides full control of access to all hosted information
- Single Sign-on: Supported through standard protocols, including SAML 2.0
- Account Authentication: User authentication is handled with a username and password through Auth0. In addition, SSO available for user accounts created through Google and Microsoft accounts. JSON web tokens (JWT) opaque token is used for authenticating all communication between User Interface and backend. API Authentication uses an oauth based JWT token generation API which generates an ephemeral token to authenticate the API calls to the Symbl.ai environment.
- Password Policies: Required strength factors (minimum characters, required numbers and special characters, common passwords rejected), salted and hashed password storage, and password resets
- Granular Access Control and Review: Role-based access, visibility and user access rights. Regular access review and analysis
- Audit and Access Logging: Detailed tracking and audit logging of all activities related to the application environment and administrative activity.
Software Development Practices
Security processes and have been fully integrated into the Symbl.ai software development processes. Developers receive training that focuses on OWASP specific guidelines. In addition, processes are setup to allow for separation of duties and segmentation of platforms with dev, staging, and production.
- OWASP based security controls design
- Separation between dev, staging, and prod
- Use of test data in development environment
- Code peer review
- Penetration testing
- Code repository controls
- Threat modeling
- Deployment controls
Infrastructure Security
Symbl.ai leverages Google Cloud Platform (GCP). We utilize hardening practices from the Center for Internet Security (CIS) Benchmarks for the platform configuration. Symbl.ai can make available all standards, GCP certifications and accreditations along with physical security controls.
Company Policies and Procedures
Symbl.ai security, risk, and compliance processes were developed based on industry best practices and are reviewed and updated on an annual basis or upon any significant change.
- Security Policies and Training – All employees go through required training upon hire and must recertify on an annual basis. Policies include:
- Acceptable Use
- Access Control
- Anti-Virus
- Backup
- Clear Desk
- Compliance
- Cryptographic Controls
- Email Security
- Equipment Handling
- HR Security
- Internal Audit
- Internet Access
- Data Destruction
- Mobile Devices
- Password
- Physical Security
- Supplier Security
- Third Party Access
- WhistleBlower
- Platform Security – On-going security activities, including:
- Network intrusion detection
- Regular external vulnerability scanning
- Penetration testing
- System, network, application log analysis, reporting, and retention
- Incident Response Planning & Team in place to handle any significant security event to triage and respond to establish system resiliency, minimize impact, and protect customer data.
Data Retention: Symbl.ai retains customer information for as long as the account is active, or as long as needed to provide a customer or sponsoring organization with specific requested services. Customers wishing to cancel an account or notify Symbl.ai to cease use of customer information to deliver services should contact [email protected].
Symbl.ai will retain and use customer information as necessary to comply with legal obligations, resolve disputes, and enforce agreements.
Regular Third-Party Security Review that identifies and evaluates security risks of vendors and third parties.
Standards and Certification
Symbl.ai is committed to establishing and maintaining compliance with key information security and regulatory standards, including:
- Service Organization Control (SOC) 2
- CSA Controls Matrix
- ISO 27001
- HIPAA
- PCI DSS
- GDPR
Symbl.ai and third-party certification and verification reports are available for limited distribution and shared under non-disclosure agreements.
Helpful Links
- CSA Security Standards – https://cloudsecurityalliance.org/star/
- Google Risk and Compliance – https://cloud.google.com/security/
- Symbl.ai Privacy Policy – https://symbl.ai/privacy-policy/
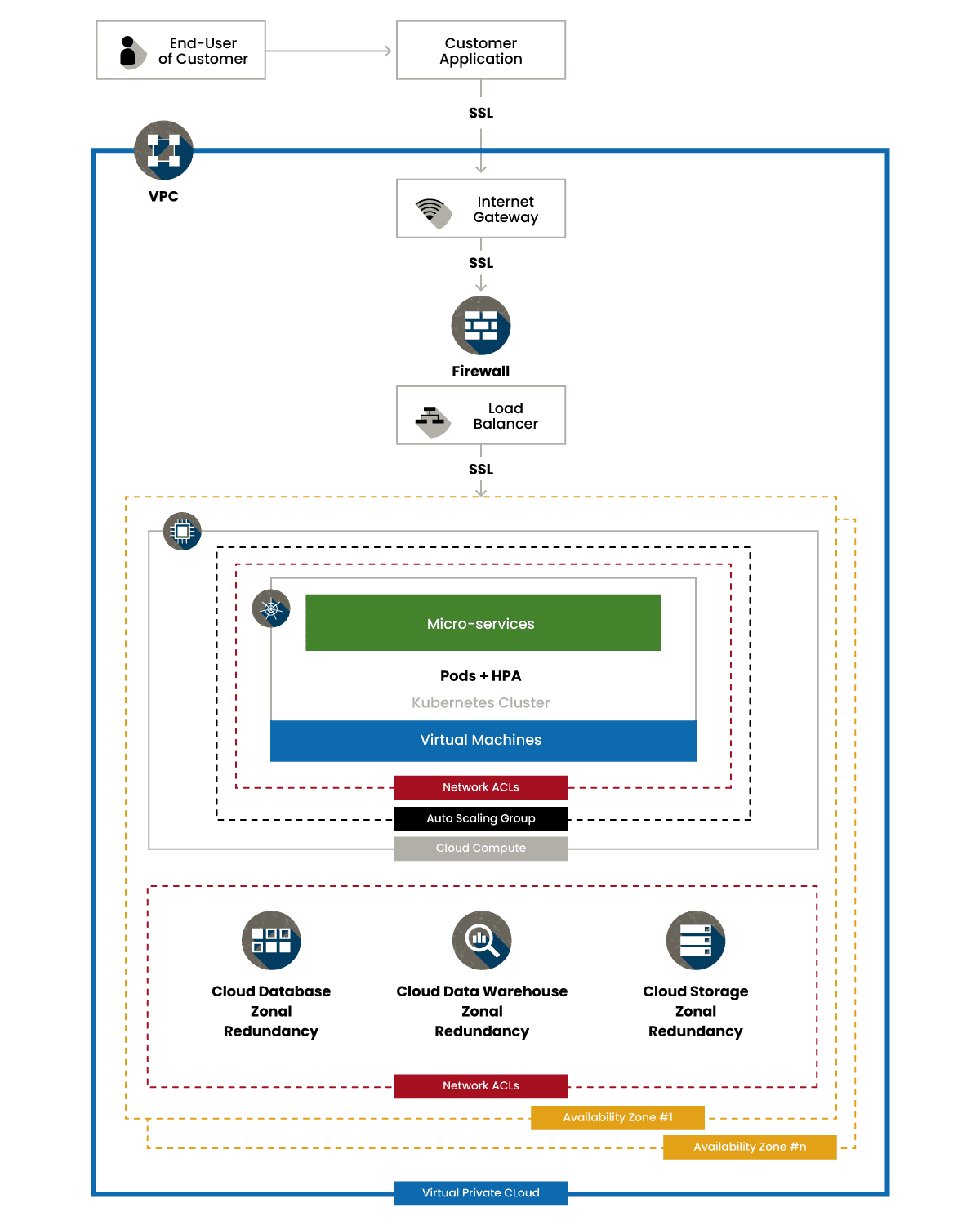
Architecture Diagram